The Ultimate Guide to HIPAA-Compliant Cloud Infrastructure
Table of Contents
HIPAA-compliant cloud infrastructure is the backbone of modern healthcare marketing and patient engagement.
Published on September 30, 2025
Every analytics, personalization, and engagement system depends on a secure, compliant hosting foundation. In the post-OCR Risk Analysis Initiative era, the stakes for getting it wrong are higher than ever.
In July 2025, behavioral health provider Deer Oaks paid a $225,000 settlement after a cloud server misconfiguration left patient data exposed online for over a year. OCR found the organization had failed to conduct a proper risk analysis, a basic requirement under HIPAA’s Security Rule, and required a two-year corrective action plan.
For healthcare organizations, this isn’t just an IT problem. These missteps can have far-reaching effects.
This guide equips marketing, IT, and compliance teams to navigate privacy-first healthcare marketing. We examine HIPAA-compliant cloud infrastructure through a dual lens:
Privacy & Compliance Utility – the extent to which the platform offers HIPAA-eligible services, facilitates secure deployment, and simplifies adherence to the shared responsibility model.
Performance Utility – the platform’s ability to support flexible, scalable, and integrated marketing operations without compromising security.
What You’ll Find Here and What You Won’t
This guide clarifies how cloud infrastructure choices affect both compliance and marketing agility in regulated healthcare environments. It is vendor-neutral, evidence-backed, and grounded in real-world implementation challenges.
Keep an eye out for Wheelhouse-specific insights, points of view, and advice, as you move through the guide:




What Is a HIPAA-Compliant Cloud Infrastructure?
A HIPAA-compliant cloud infrastructure can support the storage, processing, and transmission of protected health information (PHI) in compliance with the HIPAA Privacy, Security, and Breach Notification Rules. These platforms can be public, private, or hybrid cloud environments, and may be delivered as Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), or managed hosting.
In healthcare, such infrastructure can provide the foundation for any application, website, analytics engine, or marketing tool that touches PHI.
Compliance readiness is demonstrated through technical capabilities and operational safeguards, not just vendor assertions. It must offer:
- HIPAA-eligible services and configurations
- Security controls such as encryption in transit and at rest, access control (down to column- and row-level), and logging
- Physical and network isolation to prevent unauthorized access
- Administrative controls such as risk management, breach response support, and workforce training resources
A true HIPAA-compliant infrastructure serves as an enforceable privacy and security layer in your stack. It ensures that workloads containing PHI are deployed in secure, isolated environments.
HIPAA-compliant cloud infrastructure is not just about a signed BAA or an IT policy. It is about creating an environment where compliance and performance work together. The winners will be the organizations whose marketing and IT teams co-own infrastructure strategy, selecting and configuring platforms to deliver both airtight PHI protection and the agility to run modern, data-driven campaigns at full speed.
Why HIPAA-Compliant Cloud Infrastructure Matters in Healthcare
Healthcare data is among the most sensitive information any organization can manage, from clinical records and diagnostic images to appointment histories, insurance details, and behavioral engagement data. In a digital-first world, this information powers not just care delivery but also the marketing, outreach, and patient experience programs that keep patients engaged.
While the legal risks of non-compliant or misconfigured cloud infrastructure are significant, so are the implications on performance marketing:
- Campaign delays – Compliance reviews stretch for weeks when environments are not pre-validated for HIPAA, causing launches to miss critical windows.
- Attribution blind spots – Without PHI-safe analytics pipelines, you cannot measure full patient journeys or prove ROI for campaigns.
- Personalization limits – Insecure infrastructure can block the use of consented data for segmentation, leaving marketing teams with generic, less effective outreach.
- Trust erosion – A breach tied to marketing systems can undermine years of brand equity and patient confidence.
As outlined earlier, HIPAA requires a comprehensive set of safeguards. When applied to cloud environments, these controls directly influence how marketers collect, process, and act on PHI.
The stakes are high. A single misconfigured storage bucket or unsecured database can result in unauthorized disclosure of PHI, triggering breach notifications, regulatory penalties, and reputational harm. In healthcare marketing, even seemingly harmless analytics data such as page title or URL can qualify as PHI if it can be tied to an individual.
Here’s what HIPAA-compliant infrastructure enables:
- Secure environments for PHI with encryption, isolation, and access controls built in
- Rapid scalability for seasonal campaigns or public health initiatives
- Compliant integration among marketing tools, analytics platforms, and EHR systems under a shared security model
- Simplified compliance audits with logging, monitoring, and documented controls
- Reduced operational risk by embedding security best practices into the default configuration
Without properly configured HIPAA-compliant infrastructure, even the best intentioned MarTech stack becomes vulnerable the moment it touches patient data. Cloud infrastructure is not just a technical choice. It is a marketing performance decision that determines the safety, speed, and effectiveness of everything built on top of it.
Role in the Healthcare Stack
From a marketer’s perspective, HIPAA-compliant cloud infrastructure is not just the IT department’s domain. It is the secure foundation that determines whether your campaigns, personalization efforts, and analytics can run at its full potential while staying compliant.
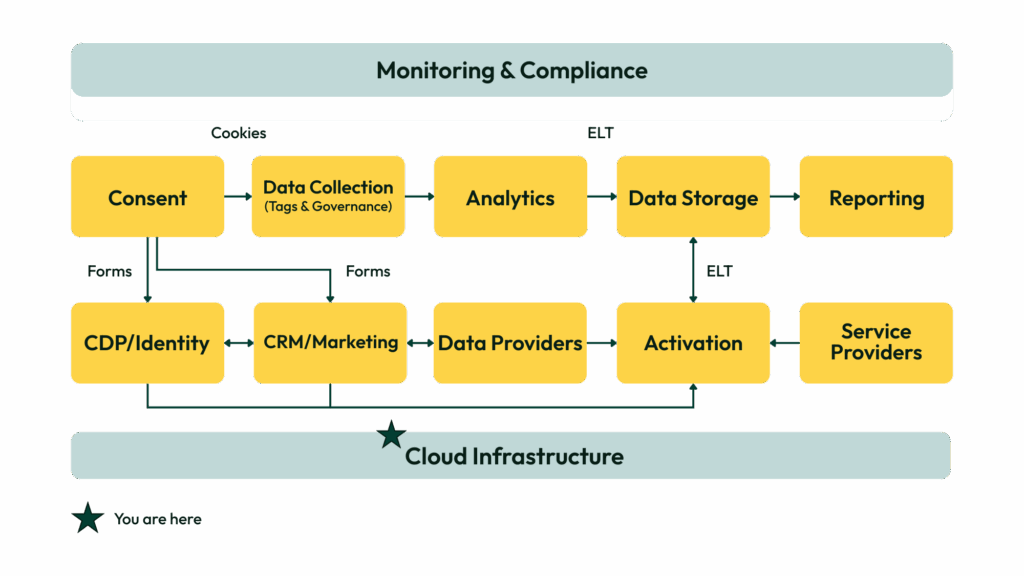
The Marketing Infrastructure Layer
In a privacy-first environment, marketers depend on HIPAA-compliant cloud platforms to:
- Host PHI-safe analytics environments for campaign measurement and ROI tracking
- Power server-side integrations with CDPs, CRMs, and personalization engines
- Enable first-party data strategies without third-party tracking risks
- Host first-party tagging servers to bypass ad blockers, which primarily target third-party network requests
- Provide scalable environments for seasonal spikes, event-driven campaigns, and public health initiatives
Critical Integration Points
To function effectively, CMPs must integrate with:
- EHR-connected campaigns – Securely pulling data for reminders or follow-up care
- Analytics and BI dashboards – Feeding KPIs from HIPAA-ready data lakes
- Preference management – Syncing consent and communication preferences into marketing tools
- Secure file sharing – Allowing creative teams to work with patient-approved content without risk
As explored further in Section XII, alignment between marketing and IT is key to maximizing both agility and compliance.
Core Capabilities
Capabilities fall into two critical domains: compliance safeguards and marketing performance enablement.
Compliance Safeguards
These are the non-negotiable requirements for any cloud platform used to store, process, or transmit PHI. They form the foundation for HIPAA compliance and enable marketing teams to confidently use patient data without legal or operational risk.
HIPAA-Eligible Services & BAA Support
The platform must support HIPAA-eligible services and have a signed BAA in place. It should also clearly outline the shared responsibility model, so all teams understand their compliance obligations.
Resilience & Breach Preparedness
- The platform should provide geographically redundant backups and tested disaster recovery processes to preserve both uptime and compliance.
- RTO and RPO commitments must ensure patient-facing applications and campaigns remain available during incidents.
- Breach detection and response support should be built into the platform to meet regulatory reporting deadlines and enable fast, coordinated marketing responses when needed.
Security & Access Controls
- Encryption in transit and at rest must be enforced for all PHI data flows.
- Logical isolation of PHI workloads is required to prevent data leakage and enable compliant mixed-use environments. This can be implemented through private cloud infrastructure or certified multi-tenant architectures.
- Role-based access controls must be configurable so only authorized team members can view or work with PHI-linked data.
- Multi-factor authentication and private access to storage and services must be supported.
Auditability & Monitoring
- The platform must maintain immutable audit logs of every access or modification to PHI.
- These logs must be retrievable on demand by compliance teams without delaying campaigns or analytics operations.
- Continuous monitoring and alerting should be built in to detect unauthorized access or potential misconfigurations.
Data Retention & Governance
- Retention of logs and PHI-related records must meet HIPAA and state-level requirements (e.g., CPRA).
- Administrative controls should support proper configuration governance, access reviews, and change tracking over time.
Marketing Performance Enablement
Once compliance is ensured, the platform must also support modern, agile healthcare marketing operations. These capabilities ensure that performance, scalability, and integration don’t suffer in the name of security.
Scalability & Speed
- The platform should support elastic infrastructure that automatically scales during campaign spikes or seasonal traffic. Note that this is table stakes for the largest infrastructure providers.
- Low-latency connections and edge delivery (e.g., via CDN) are critical for responsive experiences, especially for nationwide audiences.
- The infrastructure must be tested and performant under compliance constraints to ensure marketing operations aren’t slowed by security overhead.
Marketing & Analytics Integration
- The platform should provide secure APIs and granular data sharing controls for connecting to CRMs, CDPs, analytics tools, and personalization engines, all while enforcing consent preferences.
- It must support server-side data collection and activation, ensuring PHI never leaks through client-side tools.
- Privacy-safe data pipelines should allow for audience segmentation, journey analytics, and campaign measurement, all within HIPAA-compliant parameters.
Developer Enablement & Automation
- Support for infrastructure as code, automation tools, and SDKs ensures teams can deploy and update marketing environments rapidly and consistently.
- Preconfigured HIPAA-compliant templates or blueprints can significantly reduce setup time and risk of misconfiguration.
When these compliance and performance capabilities are built into the infrastructure, marketing teams can confidently run high-impact campaigns knowing the platform protects PHI and enables agile, modern execution. For a quick reference to required safeguards and technical criteria, see our HIPAA Cloud Compliance Evaluation Checklist.
HIPAA Cloud Provider Vendor Landscape
For marketers, the key is choosing a platform that not only protects PHI but also enables fast, integrated, and data driven campaigns.
Enterprise Cloud Leaders
Amazon Web Services (AWS)
- Broad portfolio of HIPAA-eligible services and global scalability.
- Strong compliance posture with encryption, access control, and logging capabilities.
- Vast partner ecosystem for marketing integrations, analytics, and personalization engines.
- Requires skilled configuration to avoid missteps that can stall campaign execution.
Microsoft Azure
- Extensive HIPAA compliance support with hybrid cloud options.
- Deep integrations with Microsoft 365, Dynamics, and Power BI for marketing analytics.
- Strong scalability for national campaigns and patient engagement initiatives.
- Complex service catalog may require dedicated governance to maintain compliance.
Google Cloud Platform (GCP)
- HIPAA-eligible core services with strengths in analytics, AI, and machine learning.
- BigQuery, covered under the Google Cloud BAA, is a standout offering for AI-driven data models, large-scale reporting, and advanced analytics.
- Attractive for marketing teams using advanced attribution modeling or predictive segmentation.
- Smaller healthcare footprint than AWS or Azure but rapidly expanding.
Healthcare-Specialized Providers
ClearDATA
- Fully managed HIPAA-compliant cloud environments purpose-built for healthcare.
- Strong default configurations that reduce the compliance burden for marketing teams.
- Slightly less flexible for non-healthcare workloads but highly reliable for PHI-sensitive campaigns.
Rackspace (Healthcare Cloud)
- Managed HIPAA hosting with support for AWS, Azure, and GCP deployments.
- Focus on operational reliability and security assurance.
- Best fit for organizations that want expert oversight of compliance while retaining multi-cloud flexibility.
Other HIPAA-Ready Providers
IBM Cloud
- HITRUST-certified HIPAA environments with strong security controls.
- Solid for regulated workloads, though less commonly used for cutting-edge marketing integrations.
Oracle Cloud Infrastructure (OCI)
- HIPAA-compliant hosting with high database performance.
- Best suited for organizations with heavy Oracle workloads or complex PHI data architectures.
Evaluation Framework
To assess HIPAA-Compliant Cloud Infrastructure & Hosting Platforms, we evaluate vendors against five weighted criteria:
Privacy & Compliance (30%)
- BAA availability (standard vs. case-by-case)
- HIPAA-compliant default configuration
- Encryption at rest and in transit
- Audit logging and role-based access
- Compliance support for HITRUST, SOC 2, etc.
Healthcare Fit (25%)
- Proven use in healthcare or medtech (case studies, vertical messaging)
- Support for regulated workloads (patient portals, AI/ML with PHI)
- FHIR-native services or health-specific APIs
Architecture & Flexibility (20%)
- Multi-cloud, hybrid, or private deployments
- Customizable security and compliance policies
- Developer-friendliness (SDKs, APIs)
- Configurable data residency options
Security & Resilience (15%)
- High availability and geographic failover
- Disaster recovery and backup automation
- Threat detection and real-time monitoring
- Zero Trust security principles
Usability & Support (10%)
- Compliance management portal or dashboard
- Preconfigured HIPAA blueprints/templates
- Dedicated healthcare support team or onboarding services
- Training, documentation, uptime SLAs
Vendor Scoring – Top Vendors
To help teams select the right HIPAA-compliant cloud platform, we’ve translated our evaluation framework into a scorecard that reflects both compliance strength and marketing performance potential. Among the three most widely used platforms, AWS, Azure, and Google Cloud Platform (GCP), each offers a different balance of capability and risk.
Amazon Web Services (AWS)
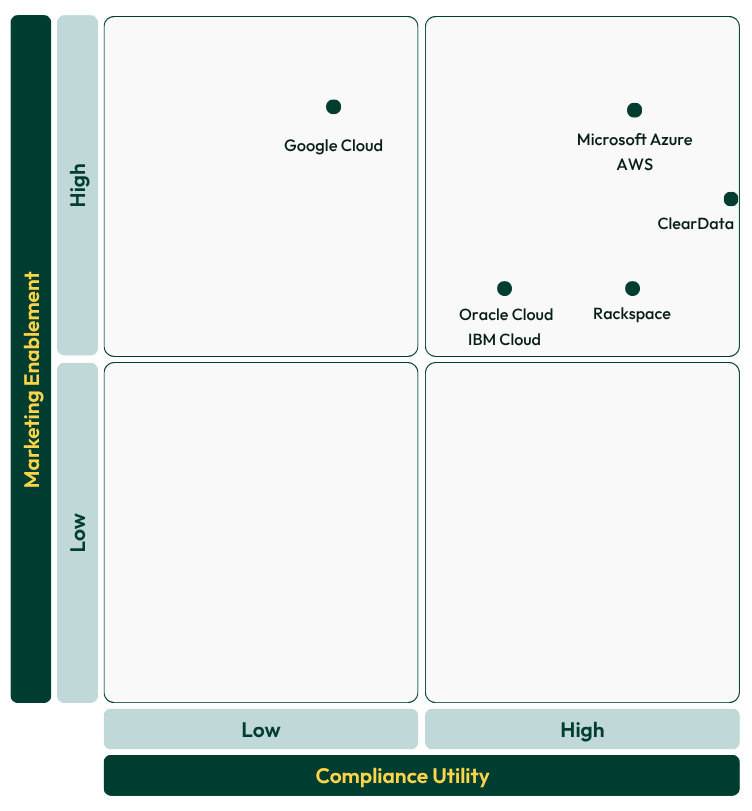
AWS received the highest overall score due to its extensive HIPAA-eligible service portfolio, strong global infrastructure, and flexible architecture. It scored high across all five framework categories, especially in Privacy & Compliance and Architecture & Flexibility.
Its Compliance Utility score reflects robust controls (encryption, logging, isolation) and a well-defined shared responsibility model—but also acknowledges the internal configuration burden. Performance Utility is high thanks to its scalability, speed, and deep marketing ecosystem, though complexity can slow less experienced teams.
Microsoft Azure
Azure scored just below AWS overall. It matches AWS in HIPAA compliance coverage and exceeds it in Microsoft-native integration (Power BI, Dynamics, etc.). It performed strongly in Security & Resilience and Healthcare Fit, but its broad catalog and complex deployment options slightly lowered Usability & Support.
Compliance Utility is high due to rich templates and encryption-by-default. Performance Utility reflects Azure’s ability to support scalable, integrated marketing environments, though governance and setup time can vary.
Google Cloud Platform (GCP)
GCP scored well overall on the Total Score due to its outstanding analytics and AI capabilities (BigQuery, Vertex AI) and strong architecture flexibility. However, its Compliance Utility Score is only 3 because HIPAA coverage is limited to a subset of core Google Cloud services. Tools commonly used by marketers—such as Google Analytics, Firebase, and certain AI APIs—are explicitly excluded from Google’s BAA and cannot be safely used with PHI without extensive workarounds or isolation.
This low compliance score reflects the high risk of missteps for organizations that don’t have rigorous governance or technical expertise to restrict usage only to HIPAA-eligible services.
Its Performance Utility Score of 7 reflects the platform’s exceptional scalability, AI-driven analytics, and ability to power advanced attribution or predictive segmentation for marketing teams that do maintain strict compliance boundaries.
Vendor Scorecard
To support direct comparison and procurement decision-making, we have translated the evaluation rubric into a vendor scorecard. This table summarizes how each HIPAA-Compliant Cloud Infrastructure vendor performs across privacy, performance, architecture, healthcare fit, and usability criteria.
Dual Utility Compliance vs. Performance
In healthcare, cloud infrastructure is typically assessed for compliance. This is logical given its role in securing PHI, meeting HIPAA’s required safeguards, and providing the audit trails necessary for regulatory review. However, the right HIPAA-compliant cloud platform not only reduces risk, it can also enable marketing agility, patient engagement, and operational efficiency.
When implemented correctly, HIPAA-compliant cloud infrastructure supports:
Compliance Utility
- BAA-backed service agreements that define shared responsibilities
- HIPAA-eligible services with encryption, logging, and isolation capabilities
- Security monitoring and alerting for PHI-related workloads
- Audit logging and retention aligned to HIPAA and state requirements
Performance Utility
- Elastic scalability to handle traffic surges from campaigns, events, or public health initiatives
- Global availability with low-latency access for multi-state or international patient populations
- Integration readiness for analytics, personalization, and secure marketing activation
- Developer enablement with APIs, automation, and infrastructure-as-code
Navigating the Compliance-Performance Tradeoff
The tension between maximum security and maximum flexibility is real. Restrictive settings slow innovation, delay launches, and hinder marketing. On the other hand, relaxing controls for convenience can expose PHI and violate HIPAA requirements.
The most effective strategies aim to harmonize both goals:
- Implement security controls as code so they scale with the environment
- Use automated compliance checks to prevent drift from HIPAA-aligned configurations
- Choose providers with certified HIPAA-eligible services that do not compromise on speed or availability
- Architect for segmentation of workloads so high-security environments do not bottleneck non-PHI use cases
Visualizing HIPAA Cloud Positioning: Compliance vs. Performance
To help illustrate where vendors fall across this dual utility spectrum, we have developed a 2×2 matrix that maps HIPAA-compliant cloud infrastructure and hosting providers based on:
- Compliance Utility: How well the platform meets HIPAA requirements, enforces security controls, and provides auditability for PHI workloads.
- Performance Utility: How well it supports scalability, integration with marketing and analytics systems, and flexible workload deployment without compromising compliance.
The matrix reveals four quadrants:
- Top-right (High Compliance, High Performance): Ideal platforms that combine rigorous HIPAA compliance with strong scalability, integration capabilities, and marketing enablement potential.
- Bottom-right (Moderate Compliance, High Performance): Platforms that deliver strong scalability and integration but may require additional configuration or controls to reach full HIPAA assurance.
- Top-left (High Compliance, Moderate Performance): Platforms engineered for healthcare-grade security that may limit flexibility or speed for marketing workloads.
- Bottom-left (Moderate Compliance, Moderate Performance): Platforms with gaps in both compliance posture and marketing integration readiness, and that may require significant remediation before use in HIPAA-regulated environments.
CMP Vendors: Privacy vs. Performance
Implementation Guidance
Choosing the right HIPAA-compliant cloud platform is only the first step. To achieve both compliance and marketing agility, the implementation process must be deliberate, collaborative, and aligned to campaign objectives from day one.
1. Align Marketing and IT Early
- Bring marketing, IT, and compliance together at the start of vendor onboarding.
- Define which marketing use cases will require PHI processing (e.g., segmentation, personalization, attribution).
- Confirm that all required services for those use cases are HIPAA-eligible and covered by the BAA.
2. Use Preconfigured HIPAA Templates Where Possible
- Many providers like AWS offer HIPAA-compliant reference architectures, deployment blueprints, or managed configurations.
- Leveraging these can shorten setup time and reduce the risk of compliance gaps.
3. Separate PHI and Non-PHI Workloads
- Isolate PHI-processing environments from general marketing workloads.
- This prevents non-PHI campaign activities from inheriting unnecessary compliance constraints while keeping PHI secure.
4. Implement Access and Monitoring Controls Upfront
- Assign role-based permissions so only authorized team members can access PHI-connected analytics or campaign data.
- Turn on logging, monitoring, and alerting at deployment to avoid retroactive compliance fixes.
5. Prioritize Server-Side Integrations
- Shift data collection, personalization logic, and analytics processing to server-side environments.
- This improves performance, enhances attribution accuracy, and ensures PHI is handled in a secure, compliant manner.
6. Test with Realistic Campaign Scenarios
- Run test campaigns that mimic actual marketing workflows before launch.
- Validate that data flows, segmentation, and reporting operate as expected in the HIPAA environment.
7. Maintain Continuous Compliance
- Schedule regular audits of configurations, permissions, and integrations.
- Monitor for service updates or changes that may impact HIPAA eligibility.
Future Outlook
The HIPAA-compliant cloud infrastructure market is evolving rapidly, with trends that will directly impact
healthcare marketers over the next three to five years. These shifts will redefine how privacy and performance are balanced, and how marketing teams collaborate with IT to leverage secure infrastructure as a competitive advantage.
1. Expansion of Healthcare-Specific Cloud Services
Major providers are investing in health data APIs, FHIR-native services, and analytics tools designed for regulated workloads. This will lower the technical barriers for marketers to activate PHI-safe personalization and measurement.
2. Growth of Privacy-Preserving Analytics
Expect more adoption of secure multiparty computation, differential privacy, and synthetic data generation. This will enable marketers to glean insights from PHI-linked datasets without directly exposing sensitive data.
3. Automation of Compliance Monitoring
Infrastructure-as-code and automated policy enforcement will become standard. This will reduce the manual overhead of compliance reviews and allow campaigns to launch faster without risk.
4. Increased Convergence of IT and Marketing Infrastructure
As server-side data collection becomes a core marketing requirement, HIPAA-compliant infrastructure decisions will move further into the marketing domain. Teams that integrate these decisions into campaign planning will gain speed and agility.
5. Rising Expectations for Vendor Accountability
Regulators and covered entities will place more responsibility on cloud vendors to proactively detect and prevent PHI breaches. This will make vendor selection, and ongoing vendor performance monitoring, even more critical.
Hard Truths From The Field
- A BAA alone does not make you compliant. Signing a BAA with AWS, Azure, or GCP does not automatically make your workloads HIPAA compliant. The configuration, monitoring, and governance of those workloads determine whether you meet HIPAA’s technical safeguards.
- IT-first decisions can cripple marketing performance. Platforms selected purely for IT or enterprise needs may lack the flexibility to support PHI-safe analytics, attribution, or personalization. This can slow down campaigns, reduce measurement accuracy, and limit targeting options.
- Server-side is only as compliant as its configuration. Moving analytics and data processing server-side can improve privacy, but if the infrastructure is misconfigured, such as leaving data buckets public or not encrypting at rest, it can still expose PHI and create legal risk.
About This Guide
This guide was created through a collaborative process that blended the speed and structure of AI with decades of real-world healthcare marketing experience.
We used AI tools to help us gather, synthesize, and organize foundational information about this category and the vendors included. These tools supported brainstorming, research structuring, and drafting early content sections. We also used AI to transcribe and analyze hours of interviews with our internal experts, vendor partners, and healthcare industry leaders, transforming those conversations into the practical insights shared throughout.
Every section was manually reviewed, edited, and enriched by our team to ensure accuracy, nuance, and relevance to healthcare marketers navigating complex privacy challenges. We refined the structure iteratively, using both AI suggestions and human judgment to create a guide that is clear, credible, and actionable.
While AI helped us work more efficiently, it’s the combination of technology and lived experience that gives this guide its depth and utility.
Created by Wheelhouse DMG
Resources
Legal Disclaimer: The information contained in this communication should not be construed as legal advice on any matter. Wheelhouse DMG is not providing any legal opinions regarding the compliance of any solution with HIPAA or other laws and regulations. Any determination as to whether a particular solution meets applicable compliance requirements is the sole responsibility of the client and should be made after consulting with their own legal counsel.
More Ultimate Guides
Explore our other Ultimate Guides to help you navigate your privacy-compliant MarTech needs.






